Cybersecurity in 2024: New Threats and Evolving Defense Strategies

Introduction
As we move further into 2024, the landscape of cybersecurity continues to evolve, bringing new threats and challenges. From sophisticated ransomware attacks to cunning phishing scams and supply chain vulnerabilities, businesses must stay vigilant and adapt their defense strategies. In this blog, we will analyze the latest cybersecurity trends and highlight the critical role of data backup, specifically focusing on Polar Backup’s adaptive storage, AI capabilities, and cost-effective solutions designed for large-scale data protection.
Latest Cybersecurity Trends
- Ransomware Attacks
- What It Is: Ransomware is a type of malicious software that encrypts a victim’s files. The attacker then demands a ransom to restore access to the data.
- Trend: In 2024, ransomware attacks have become more targeted and sophisticated, often focusing on critical infrastructure and large enterprises.
- Phishing Scams
- What It Is: Phishing scams involve fraudulent attempts to obtain sensitive information by disguising as a trustworthy entity.
- Trend: Phishing attacks are increasingly leveraging AI to create more convincing and personalized messages, making them harder to detect.
- Supply Chain Vulnerabilities
- What It Is: These vulnerabilities occur when attackers infiltrate an organization through its supply chain, exploiting weaker links to gain access.
- Trend: The interconnectedness of global supply chains has made these attacks more prevalent, posing significant risks to businesses.
Evolving Defense Strategies
- Advanced Threat Detection
- AI and Machine Learning: Utilizing AI and machine learning to detect and respond to threats in real-time. These technologies can identify patterns and anomalies that may indicate a cyberattack.
- Behavioral Analytics: Monitoring user behavior to detect unusual activities that could signify a breach.
- Zero Trust Architecture
- Principle: The Zero Trust model operates on the assumption that threats could be both external and internal. It requires strict verification for every person and device trying to access resources on a private network.
- Implementation: Enforcing multi-factor authentication, continuous monitoring, and micro-segmentation to limit access.
- Enhanced Incident Response Plans
- Preparation: Developing comprehensive incident response plans that include regular drills and updates based on emerging threats.
- Coordination: Ensuring coordination between IT, security teams, and external partners for effective incident management.
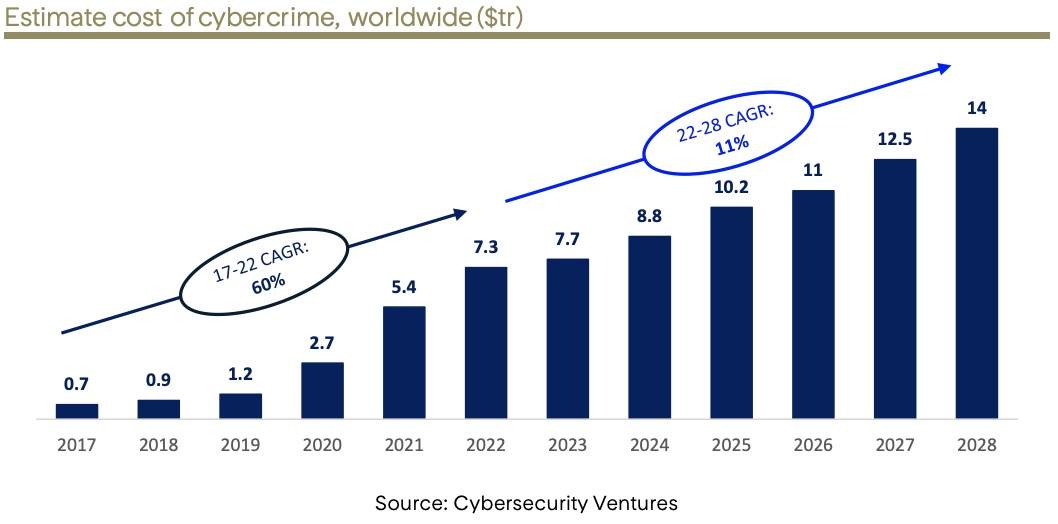
The Role of Data Backup in Cybersecurity
While advanced detection and response strategies are crucial, data backup remains the last line of defense against cyberattacks. Ensuring business continuity and rapid recovery of data can significantly mitigate the impact of an attack.
Polar Backup: A Robust Solution for Modern Cybersecurity Needs
Polar Backup offers a comprehensive solution designed to protect businesses against data loss, leveraging advanced features to ensure security and accessibility.
- Business Adaptive Storage
- Scalability: Polar Backup is designed to handle large-scale data, capable of backing up tens of terabytes efficiently.
- Adaptive Storage: The system intelligently manages data, ensuring frequently accessed files are readily available, while less-used data is stored cost-effectively.
- AI Capabilities
- Intelligent Backup: AI-driven algorithms ensure that backups are performed optimally, reducing the load on your systems and maximizing efficiency.
- Anomaly Detection: AI can detect unusual patterns in your data usage, alerting you to potential threats before they cause damage.
- Cost-Effective Solutions
- Affordable Plans: Polar Backup offers competitive pricing, making it a cost-effective solution for businesses of all sizes.
- Low-Cost Storage: By utilizing cold storage for infrequently accessed data, Polar Backup minimizes costs without compromising on accessibility or security.
Conclusion
In the ever-evolving world of cybersecurity, staying ahead of new threats requires a multi-faceted approach. While advanced threat detection, zero trust architecture, and incident response plans are essential, robust data backup solutions like Polar Backup are crucial for ensuring business continuity and data recovery. With its adaptive storage, AI capabilities, and cost-effective plans, Polar Backup is well-equipped to protect your business data against the latest cyber threats.
